Iranian hacking group used Android malware to steal 2FA codes - Android
Two-factor authentication (2FA) is only effective at adding an extra layer of account security if the device to which you receive a verification code is itself uncompromised. Otherwise, the code can be stolen to effectively bypass 2FA, which a group of Iranian hackers has been uncovered to be doing for years in targeting Iranian dissidents […] More
This article, Iranian hacking group used Android malware to steal 2FA codes, was originally published at NoypiGeeks | Philippines Technology News, Reviews and How to's.
Two-factor authentication (2FA) is only effective at adding an extra layer of account security if the device to which you receive a verification code is itself uncompromised. Otherwise, the code can be stolen to effectively bypass 2FA, which a group of Iranian hackers has been uncovered to be doing for years in targeting Iranian dissidents and activists.
According to security researcher Check Point, the Iranian group with a designated name Rampant Kitten has developed an Android backdoor malware hidden inside malicious apps to gain remote access to a victim’s Android device.

Related articles
- How to get rid of malware from your Android smartphone
- A hacked or data-breached company is no laughing matter
Once the backdoor gains a foothold in a device, it allows Rampant Kitten to read the contact list and text messages, spy on the user via the microphone, and even send texts. That last capability is how the group steals 2FA verification codes. The backdoor simply waits for a verification code to arrive in the SMS inbox and forwards the code to the group.
Besides stealing 2FA codes, the backdoor can also force the device to display phishing pages that impersonate sites such as Telegram to lure unsuspecting users into entering their usernames and passwords.
Via: ZDNet
This article, Iranian hacking group used Android malware to steal 2FA codes, was originally published at NoypiGeeks | Philippines Technology News, Reviews and How to's.
23/09/2020 11:02 AM
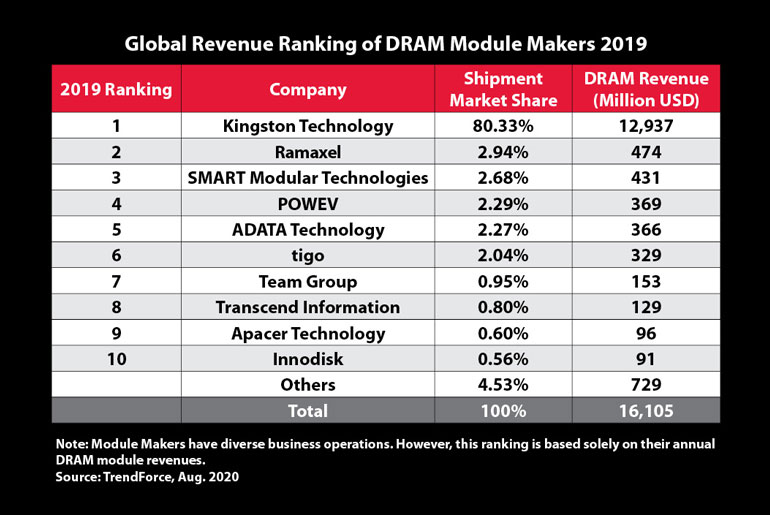
Kingston Technology crowned Top DRAM Module Supplier in 2019
23/09/2020 06:47 AM
Spotify releases nine exclusive Filipino podcasts
23/09/2020 07:00 AM
Spotify partners with nine Filipino podcasts for exclusive content
23/09/2020 01:14 AM
LG Electronics receives AHRI Performance Award for 3rd consecutive year
23/09/2020 07:53 AM
realme 7 Pro, PH’s fastest-charging smartphone, coming on Sep 30
23/09/2020 06:57 AM
SKYBIZ intros HomeBiz Plan
23/09/2020 07:45 AM
Alibaba Cloud launches New Digital Ecosystem Strategy in the Philippines
23/09/2020 03:01 PM
Get up to P6,000 cashback with HP’s Free GCash promo
23/09/2020 03:20 AM
- HEALTH
- Comics
- Libraries & Demo
- Sports Games
- Racing
- Photography
- Transportation
- Media & Video
- Sports
- Health & Fitness
- Weather
- Medical
- Cards & Casino
- Arcade & Action
- Personalization
- Social
- Communication
- Productivity
- Casual
- Shopping
- Tools
- Brain & Puzzle
- Business
- News & Magazines
- Finance
- Lifestyle
- Music & Audio
- Entertainment
- Travel & Local
- Books & Reference
- Education